The Man in the Middle Attack
After their first system was broken, instead of talking on the phone,
Michael and Nikita can now only communicate via text messages. One of
her captors, The Man, is watching each of the
transmissions; moreover, he can intercept messages and send false
messages. When Nikita sends a message to Michael announcing
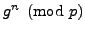 , The Man intercepts this message, and sends his own
number
, The Man intercepts this message, and sends his own
number
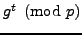 to Michael. Eventually, Michael and The Man
agree on the secret key
to Michael. Eventually, Michael and The Man
agree on the secret key
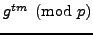 , and Nikita and The Man agree
on the key
, and Nikita and The Man agree
on the key
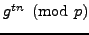 . When Nikita sends a message to Michael
she unwittingly uses the secret key
. When Nikita sends a message to Michael
she unwittingly uses the secret key
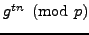 ; The Man then
intercepts it, decrypts it, changes it, and re-encrypts it using the
key
; The Man then
intercepts it, decrypts it, changes it, and re-encrypts it using the
key
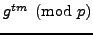 , and sends it on to Michael.
This is bad because now The Man can read every message sent between
Michael and Nikita, and moreover, he can change them in transmission
in subtle ways.
, and sends it on to Michael.
This is bad because now The Man can read every message sent between
Michael and Nikita, and moreover, he can change them in transmission
in subtle ways.
Figure 3.3:
The Man in the Middle Attack
|
|
One way to get around this attack is to use a digital signature scheme
based on the RSA cryptosystem. We will not discuss digital signatures
further in this book, but will discuss RSA in the
next section.
William
2007-06-01