Next: The Fundamental Theorem of Up: Prime Factorization Previous: The Greatest Common Divisor Contents Index
As a first example, let ![]() . The sum of the digits
of
. The sum of the digits
of ![]() is divisible by
is divisible by ![]() , so
, so ![]() is divisible by
is divisible by ![]() (see
Proposition 2.1.8), and we have
(see
Proposition 2.1.8), and we have
![]() .
The number
.
The number ![]() is divisible by
is divisible by ![]() , since its last digit
is
, since its last digit
is ![]() , and we have
, and we have
![]() . Again,
dividing
. Again,
dividing ![]() by
by ![]() , we have
, we have
![]() ,
which is the prime factorization of
,
which is the prime factorization of ![]() .
Generalizing this process proves the following proposition:
.
Generalizing this process proves the following proposition:
Two questions immediately arise: (1) is this factorization unique, and
(2) how quickly can we find such a factorization? Addressing (1),
what if we had done something differently when breaking apart ![]() as a product of primes? Could the primes that show up be different?
Let's try: we have
as a product of primes? Could the primes that show up be different?
Let's try: we have
![]() . Now
. Now
![]() and
and
![]() , and again the factorization is the same, as asserted
by Theorem 1.1.6 above. We will prove uniqueness
of the prime factorization of
any integer in Section 1.1.4.
, and again the factorization is the same, as asserted
by Theorem 1.1.6 above. We will prove uniqueness
of the prime factorization of
any integer in Section 1.1.4.
sage: factor(1275) 3 * 5^2 * 17 sage: factor(2007) 3^2 * 223 sage: factor(31415926535898) 2 * 3 * 53 * 73 * 2531 * 534697
Regarding (2), there are algorithms for integer factorization.
It is a major open problem to decide
how fast integer factorization algorithms can be.
We say that an algorithm to factor ![]() is polynomial time
if there is a
polynomial
is polynomial time
if there is a
polynomial ![]() such that for any
such that for any ![]() the number of steps needed by
the algorithm to factor
the number of steps needed by
the algorithm to factor ![]() is less than
is less than
![]() . Note
that
. Note
that
![]() is an approximation for the number of digits
of the input
is an approximation for the number of digits
of the input ![]() to the algorithm.
to the algorithm.
Peter Shor [#!shor!#] devised a polynomial time algorithm
for factoring integers on quantum computers. We will not discuss his
algorithm further, except to note that in 2001 IBM researchers
built a quantum computer that used Shor's algorithm to factor ![]() (see
[#!quantum15!#,#!ibm:shor15!#]). Building much larger quantum
computers appears to be extremely difficult.
(see
[#!quantum15!#,#!ibm:shor15!#]). Building much larger quantum
computers appears to be extremely difficult.
You can earn money by factoring certain large integers. Many
cryptosystems would be easily broken if factoring certain large
integers were easy. Since nobody has proven that factoring integers
is difficult, one way to increase confidence that factoring is
difficult is to offer cash prizes for factoring certain integers. For
example, until recently there was a $10000 bounty on factoring the
following ![]() -digit integer (see [#!rsa:challenge!#]):
-digit integer (see [#!rsa:challenge!#]):
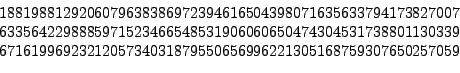
This number is known as RSA-576 since it has 576 digits when written in binary (see Section 2.3.2 for more on binary numbers). It was factored at the German Federal Agency for Information Technology Security in December 2003 (see [#!factor576!#]):
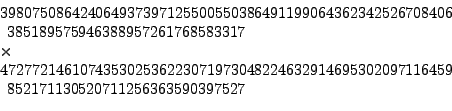
The previous RSA challenge was the
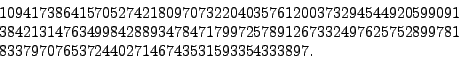
It was factored on 22 August 1999 by a group of sixteen researchers in four months on a cluster of 292 computers (see [#!rsa155!#]). They found that RSA-155 is the product of the following two
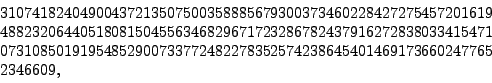
and its factorization was worth $20000 until November 2005 when it was factored by F. Bahr, M. Boehm, J. Franke, and T. Kleinjun. This factorization took 5 months. Here is one of the prime factors (you can find the other):
(This team also factored a 663-bit RSA challenge integer.)
The smallest currently open challenge is RSA-704, worth $30000:
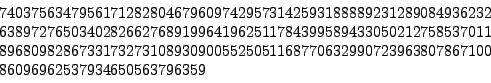
sage: n = 74037563479561712828046796097429573142593188889231289084936232638972765034028266276891996419625117843995894330502127585370118968098286733173273108930900552505116877063299072396380786710086096962537934650563796359 sage: len(n.str(2)) 704 sage: len(n.str(10)) 212 sage: n.is_prime() # this is instant False
These RSA numbers were factored using an algorithm called the number field sieve (see [#!lenstras:nfs!#]), which is the best-known general purpose factorization algorithm. A description of how the number field sieve works is beyond the scope of this book. However, the number field sieve makes extensive use of the elliptic curve factorization method, which we will describe in Section 6.3.
William 2007-06-01